Insecure HTTP Methods¶
One Liner¶
- Checking HTTP Methods
curl -i -X OPTIONS http://XXXXnmap --script http-methods --script-args http-methods.url-path='/test' $ipCurl usagecurl -X POST http://internal-01.bart.htb/simple_chat/register.php -d "uname=0xdf&passwd=password"
- Shell via Put Method
Put Shellcurl -X PUT -T "/path/to/file" "http://myputserver.com/puturl.tmp"curl -X MOVE --header "Destination:http://ip/asp.asp" "http://ip/asp.txt"
HTTP Status Codes¶
| Sr.No. | Method and Description |
|---|---|
| 1 | GET It retrieves information from a server using a given URI. It is essential that GET requests only retrieve data and do not alter it in any way. |
| 2 | HEAD Similar to GET, but only transfers the status line and header. |
| 3 | POST Data is sent to the server using this method. For example, collecting user information, file uploading etc. |
| 4 | PUT By using the PUT method, you're telling the server to store the enclosed entity under the given URI. If the URI refers to an existing resource, it gets modified, and if it doesn't, then the server creates the resource with that URI. |
| 5 | DELETE It removes the resource from target source supplied by given URI. |
| 6 | CONNECT It establishes a tunnel to the server identified by a given URI. |
| 7 | OPTIONS It shows all available methods to communicate with the server. |
| 8 | TRACE A HTTP TRACE method is used for diagnostic purposes. It will echo the exact request that was received in its response if the TRACE method is enabled. |
How to Exploit¶
To exploit any methods it is important to know which methods are enabled, for that we can simply check via OPTIONS
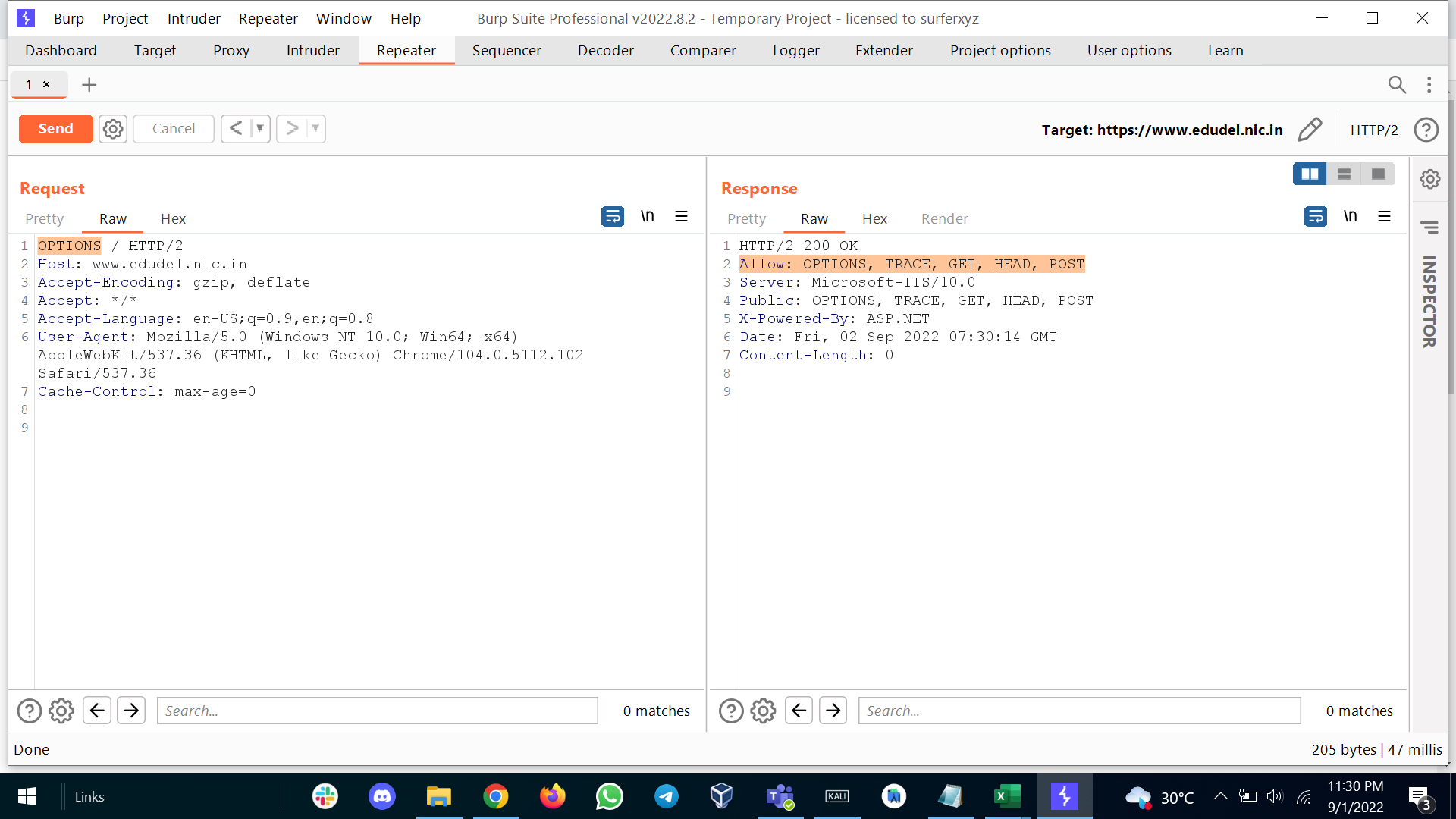
If that not worked you should definitely try by submitting random word as method. Sometime you might receive and error which shows which methods are implemented.
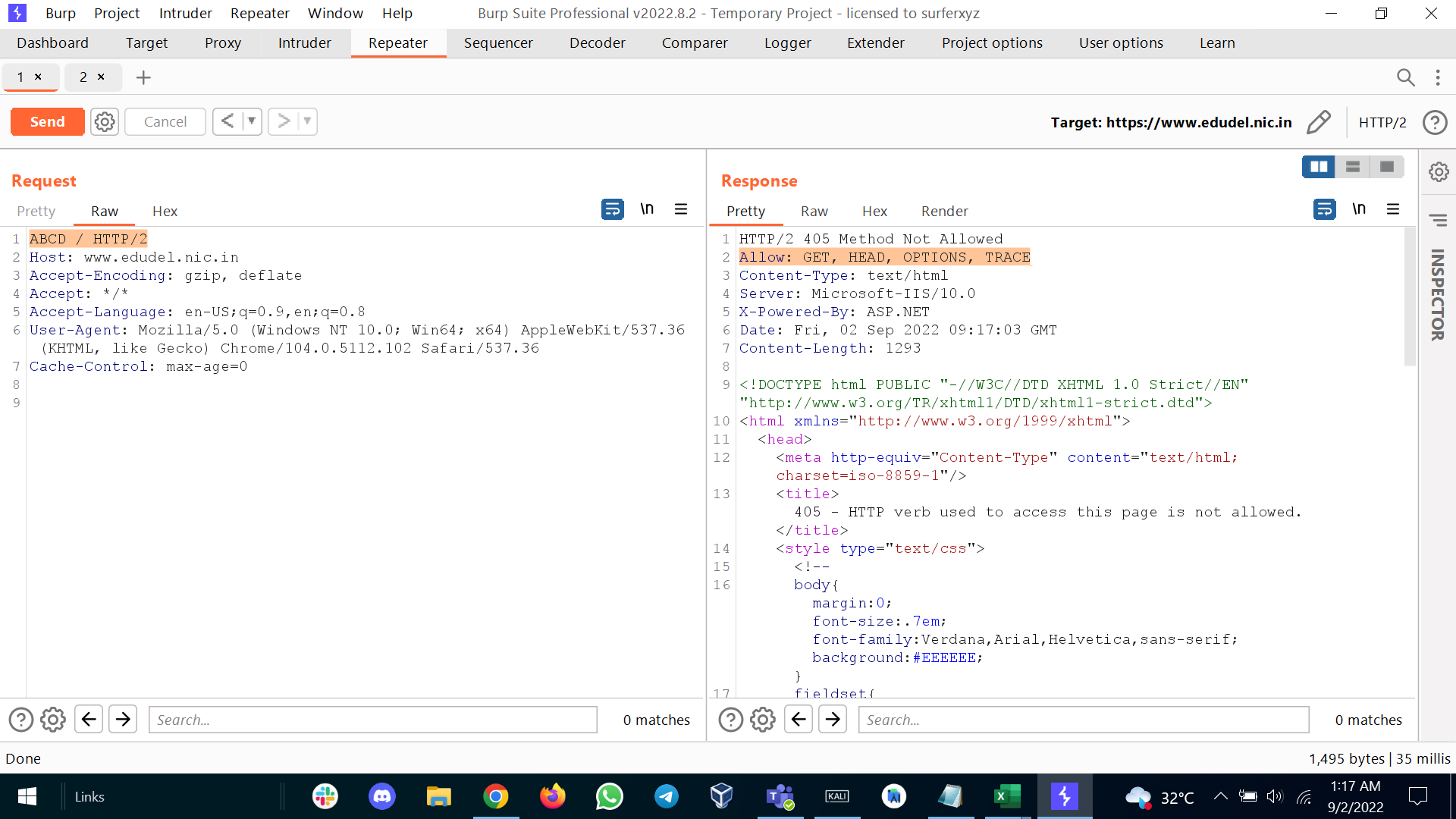
Once we got to know which methods are enabled then we will look for exploit respectively.
-
HEAD, GET, POST, and CONNEC are safe HTTP Method. Of course, the request itself may have malicious parameters, but that is separate from the exploiting http Method topic. It is always recommended that disable unnecessary methods.
-
PUT, DELETE - these methods were initially intended as file management operations. Some web servers still support these in their original format. You can change or delete files from the server's file system arbitrarily. If these are enabled, it opens you to perform some dangerous attacks. Here is the great article to exploit PUT method - https://www.arridae.com/blogs/HTTP-PUT-method.php
-
OPTIONS: As previously mentioned, we can use this method to identify which other methods are enabled so it can be considered a shortcut to finding another hole. Now, this is not a vulnerability; since there is no actual use for it, it just increases the attack surface and should ideally be disabled. Although the OPTIONS method is used for several legitimate purposes nowadays, for example, some REST APIs require an OPTIONS request, CORS requires pre-flight requests, and so on. So there are scenarios wherein OPTIONS should be enabled, but the default should still be "disabled unless required".
-
TRACE - This is also a diagnostic method that returns the entire HTTP Request in the response body. This includes the request body and the request headers, including, e.g. cookies, authorization headers, and more. Not too surprising, this can be substantially misused, such as the classic Cross-Site Tracing (XST) attack, wherein an XSS vector can be utilized to retrieve HttpOnly cookies, authorization headers, and such. This should be disabled.