Impact of Lack of Code Obfuscation¶
Failing to obfuscate code during the compilation process can expose sensitive information and increase the likelihood of successful reverse engineering by attackers. Here's how the lack of code obfuscation can impact the security of an application:
1. Code Decompilation¶
Attackers can easily decompile the application using tools like JD GUI and Dnspy, revealing the underlying source code:
Code Decompilation: 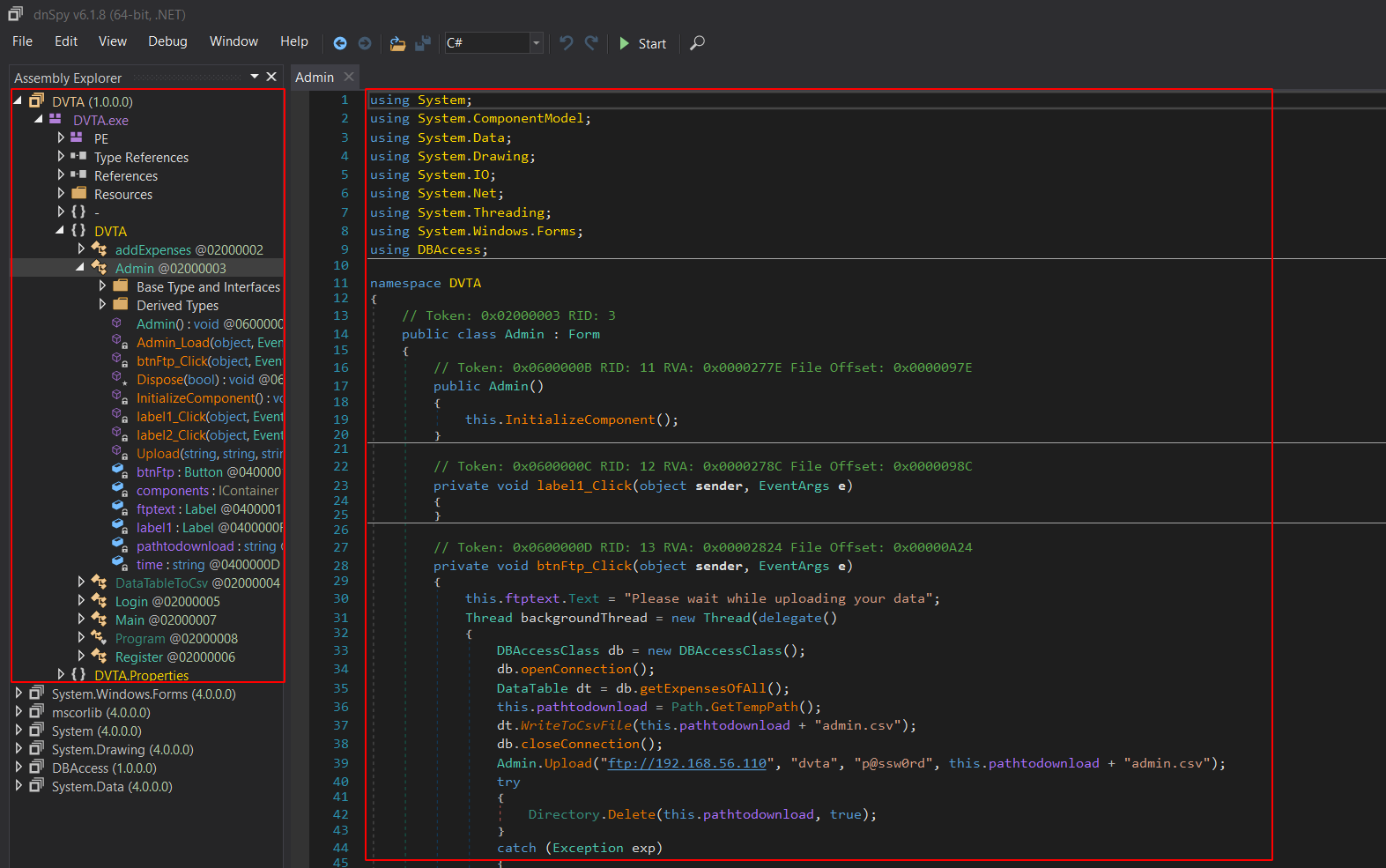
In the screenshot above, the source code of the Damn Vulnerable Thick Client App (DVTA) is decompiled using Dnspy. This exposes the application's logic, sensitive information, and potential vulnerabilities to attackers.
2. Exposure of Sensitive Information¶
- Sensitive Data Exposure: Unobfuscated code may contain hardcoded credentials, API keys, or other sensitive information, which can be exploited by attackers to gain unauthorized access to systems or data.
3. Reverse Engineering¶
- Understanding Application Logic: Attackers can analyze the decompiled code to understand the application's logic and behavior, facilitating the identification of vulnerabilities and exploitation techniques.
4. Vulnerability Exploitation¶
- Identification of Weaknesses: Exposed source code makes it easier for attackers to identify vulnerabilities such as insecure coding practices, input validation flaws, or insecure cryptographic implementations.
Mitigation Strategies¶
To mitigate the risks associated with lack of code obfuscation, consider implementing the following strategies:
-
Code Obfuscation: Utilize code obfuscation techniques to obscure the application's logic and make reverse engineering more challenging for attackers.
-
Sensitive Data Protection: Avoid hardcoding sensitive information in the source code and use secure storage mechanisms such as environment variables or secure configuration files.
-
Static Code Analysis: Conduct regular static code analysis to identify and remediate security vulnerabilities before deployment.