SSL Pinning¶
Concept¶
Pinning is an optional mechanism that can be used to improve the security of service or site that relies on SSL Certificates. Pinning allows you to specify a cryptographic identity that should be accepted by users visiting your site. SSL/TLS uses digital certificates to provide authentication and encryption. To trust that a certificate is genuine and valid, it is digitally signed by a root certificate belonging to a trusted certificate authority (CA).
Ways to Implement SSL Pinning¶
-
Certificate Pinning: In certificate pinning , the developer hardcodes some bytecode of SSL certificate into application code. When the application communicates with the server, it checks whether the same bytecode is present in a certificate or not. If it is present, the application sends a request to the server. If the bytecode does not match it will throw an SSL certificate error. This technique prevents an attacker to use his/her own self-signed certificate.
-
Public Key Pinning: In public key pinning when a customer visits a website, the server pins (by way of injecting it) its public key in client (customer’s) browser. When the client revisits the same website, the server identifies its public key to check the integrity of the connection. This technique also prevents an attacker from using his/her self-signed certificate.
Methods of certificate pinning¶
TrustManager¶
Managers are responsible for managing the trust material used when trust decisions are made, and for deciding whether credentials presented by peers should be trusted.
Creating TrustManagers is either done by using a TrustManagerFactory or by implementing one of the TrustManager subclasses.
Steps to bypass SSL Pinning¶
Frida for SSL pinning bypass¶
Requirements:
-
Python 3
-
Linux/Windows/Mac
-
Rooted android device
Connect your device to adb command shell, once connected you can push the downloaded file to your data/local/imp folder.
Now open Cmd/ Terminal & follow these steps,
If everything goes well we can make a quick check by running(this will show the processes running on device)
Here you need to have the burpsuit certificate, for that open burpsuit & go to proxy settings and click on the export certificate button, and then select “Certificate in DER format” and download it.
Once its done rename it’s extension from “.der” to “.cer”. After that, you should push this file to your android device
The last part of Frida is your JavaScript, you can write your own or copy it from here. Save it as a js file & run the command.
$ frida -U -f it.app.mobile -l frida-android-repinning.js --no-pause
Where
-U stands for "USB device"
-f stands for "Filename"
-l stands for "location of js file"
--no-pause stands for "automatically start main thread after startup"
If everything goes well, you will get an output such as
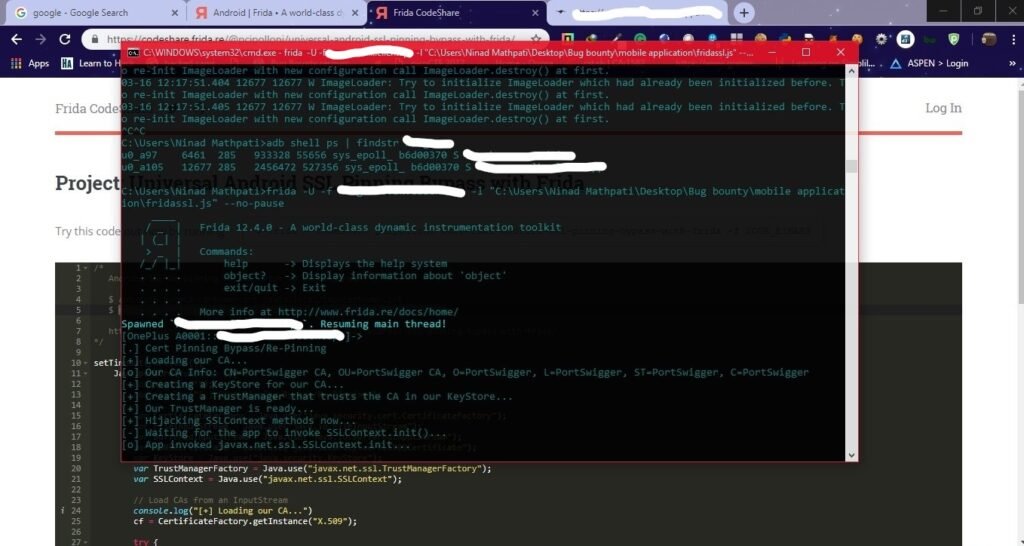
& bypass the SSL pinning.
Now, you are good to go, you can successfully intercept the requests and work on dynamic analysis. Some errors in this will be sometimes you won’t be able to bypass in 1st attempt make it 4-5 times. While attempting once again you might get an error as
“Frida server service already running“
Here you need to kill that service using the adb kill command.
This was all about Frida SSL bypass
Now let’s move towards Objection
Bypass using Objection¶
Objection is a runtime mobile exploration toolkit, powered by Frida. It was built with the aim of helping assess mobile applications and their security posture without the need for a jailbroken or rooted mobile device.
You can install it by running
Once done get your file name of the application by using Frida or adb.
then,
This will create a new apk which is hooked
Push the apk file or install the application by
Now run,
objection -g (new apk file name) explore -q
Where,
-g stands for "Name of the Frida Gadget/Process to connect to"
explore stands for "objection exploration REPL"
thus if the file is successfully injected
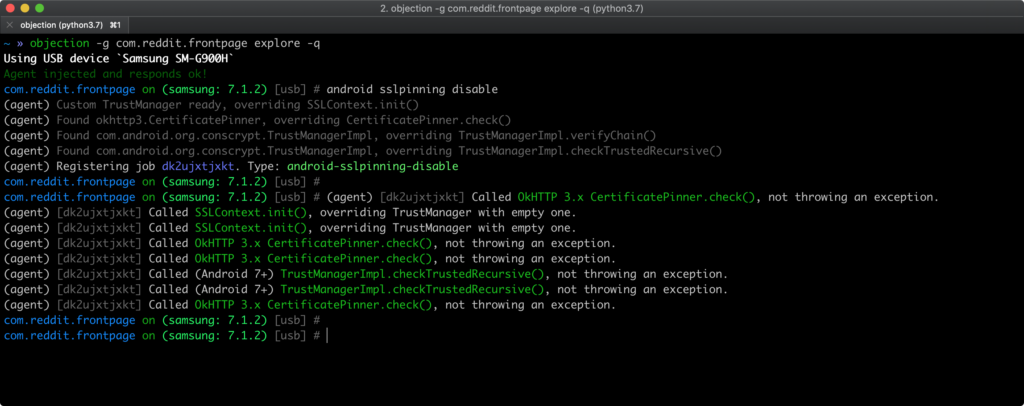
Now, you are good to go and intercept the requests through burpsuit.
Bypass using Xposed framework¶
Xposed is a framework that allows users to easily apply add-ons (called Modules) to the ROM. Rather than flashing a new ROM to get a specific feature, you can use Xposed to add individual features to whatever ROM you’re using, or even just the stock ROM.
Installation,
Download the app from here
Run it and find an application named SSL pinning bypass, install it
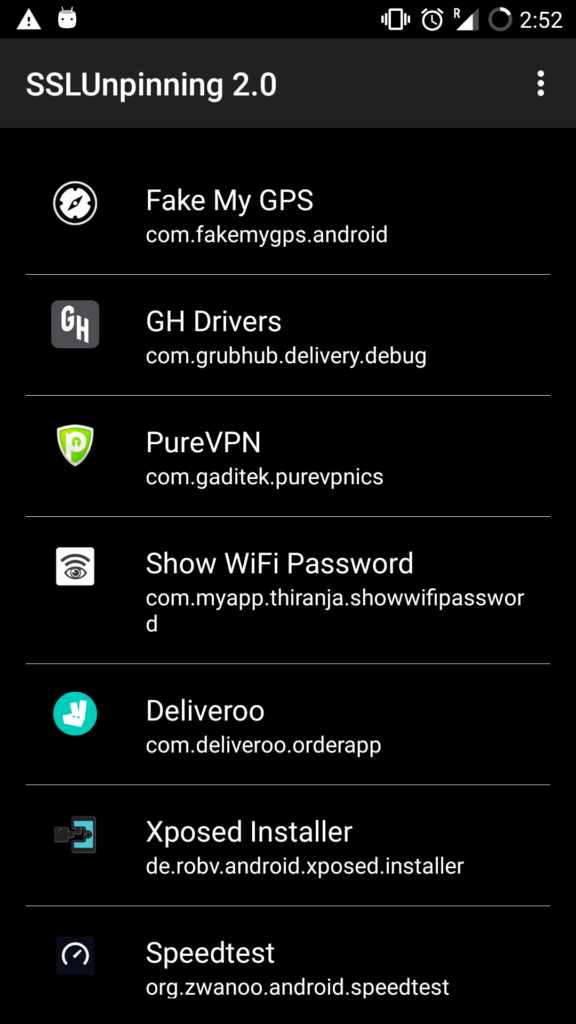
Thus click on whichever application you want to apply the SSL bypass & you are ready to go and intercept through burp request.
Bypass through manually changing the code¶
The reason why I gave a link to SSL pinning implementation above is for this one, if none of the above methods works, this should work but it’s not simple, here you need to have knowledge about the android app structure how it’s built and how it works, sometimes a developer would choose to provide their own SSL libraries instead of relying on the system libraries to handle the SSL certificate validation. So here we can decompile the apk using apktool or simply extract it. Convert the dex file to jar using the dex2jar and open that file using Java reversing tool (such as JD-GUI).
Here you need to find the code responsible for certificate validation, once you get it you can manually fix it or by using Frida you can hook the application.
Here is an awesome blog which shows a detailed way of bypassing SSL pinning using this method.
Thus, these were some methods to bypass SSL pinning in android.