Insecure data Storage¶
Insecure data storage vulnerabilities occur when development teams assume that users or malware will not have access to a mobile device's filesystem and subsequent sensitive information in data-stores on the device.
Google advice should not store any of class or executable or any senstive information to external storage because other application can bind and steal the data.
- To check any sensitive information or class store in External Storage
1. Decompile the apk to jar or unzip.
2. Look app permission in AndroidManifest.xml.
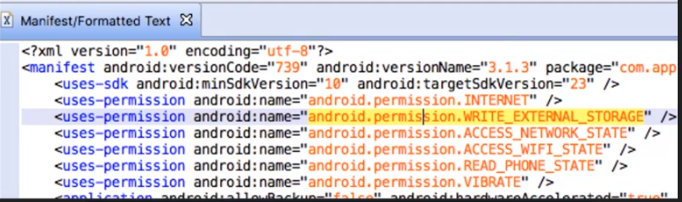
and also can search in decompile class file.

Detecting read/write to External Storage¶
inotify: monitor files to fire an event after files are accessed or changed by any process on the device.
Check vulnerability if app stores data in mnt/sdcard¶
1. Open Vulnerable app and Login or typing in input field.
2. Check the source code where application create file and giving name of the file by application.
3. Navigate to file :
4. Check the XML file if app vulnerable the entered data will be there | Developer think if they save file as .{file_name} so file will hidden and secure but it's not attacker easily escalate file.
Check vulnerability if app stores data in shared_pref¶
1. Open Vulnerable app and Login or typing in input field.
2. Navigate to:
3. Check the XML file if app vulnerable the entered data will be there.
Check vulnerability if app stores data in databases¶
1. Open Vulnerable app and Login or typing in input field.
2. Navigate to:
3. Check the XML file if app vulnerable the entered data will be there.
Check vulnerability if app stores data in temp_file¶
1. Open Vulnerable app and Login or typing in input field.
2. Check the source code where application create file and giving name of the file by application.
3. Navigate to file :
4. Check the XML file if app vulnerable the entered data will be there.
Backup the app data using adb backup command¶
We can examine the internal memory of apps on non-rooted devices using the backup feature. Now let's use the backup technique of android to find security issues by following these steps:
1. Backup the app data using the adb backup command.
We can backup an entire android phone using the following command:
We can also store only a specific app using the following command:
2. Convert the .ab format to the .tar format using the android backup extractor.
3. Extract the TAR file using the pax or star utility.
Note: Standard tools like tar and 7-Zip don't support untaring the files generated by abe.jar because they don't allow storing directories without trailing slash.
4. Analyze the extracted content from the previous step for security issues.