Server-Side Template Injection (SSTI)¶
What is SSTI?¶
SSTI stands for Server-Side Template Injection, a web application vulnerability that occurs when an attacker is able to inject malicious code into a server-side template engine. This allows them to execute arbitrary code within the context of the server, potentially leading to data theft, unauthorized access, or server compromise. SSTI vulnerabilities commonly arise when input from users is not properly sanitized or validated before being passed to the template engine, enabling attackers to manipulate the template rendering process.
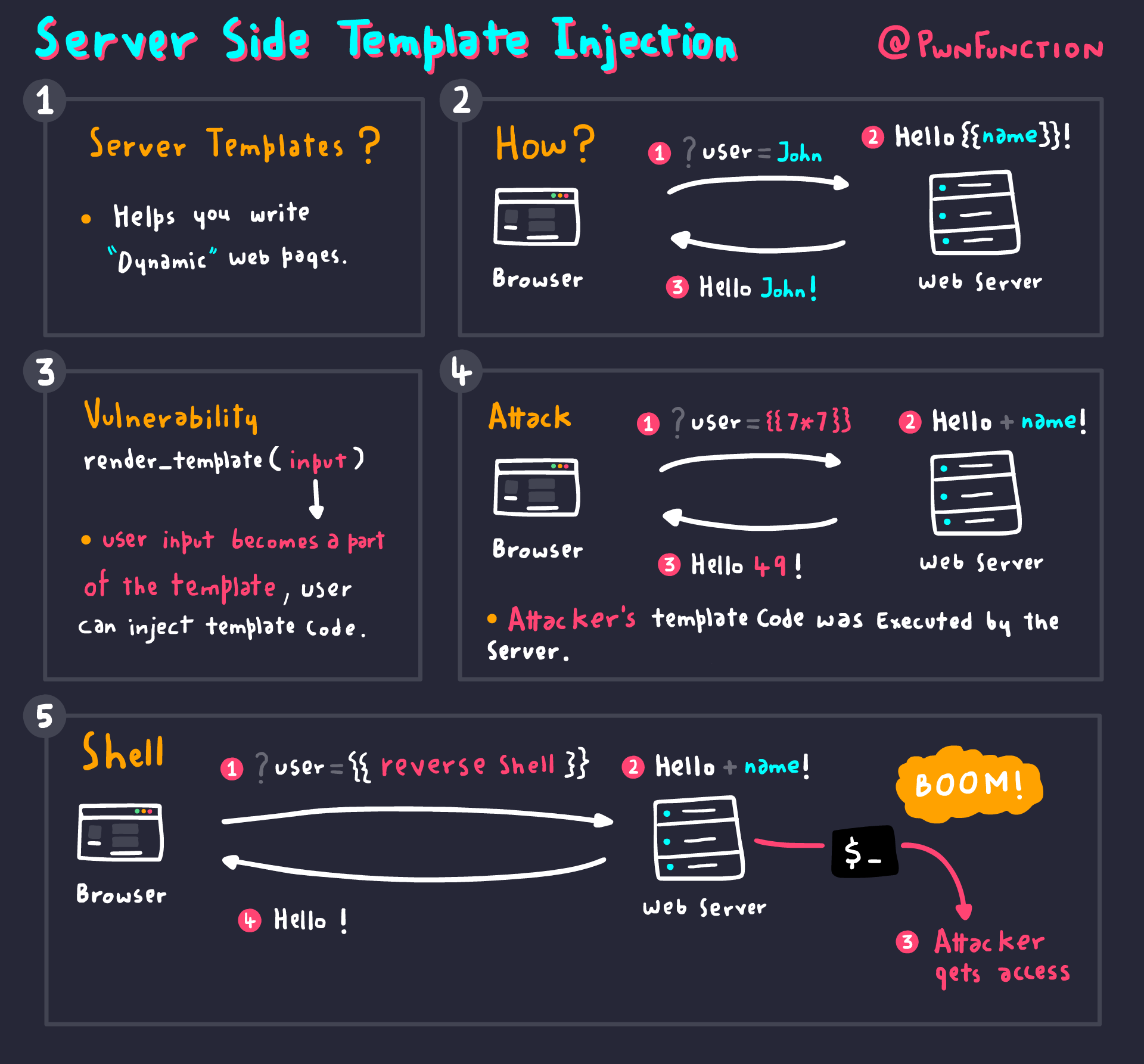
SSTI Handbook¶
References¶
-
https://www.youtube.com/watch?v=SN6EVIG4c-0&feature=youtu.be
-
https://pequalsnp-team.github.io/cheatsheet/flask-jinja2-ssti#
-
https://github.com/TeamGreyFang/CTF-Writeups/blob/master/VolgaCTF2020/Web-Newsletter/README.md
-
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection
-
https://portswigger.net/web-security/server-side-template-injection