SSL Pinning¶
SSL Pinning bypass for iOS¶
As I said we need to know the basics or atleast know how SSL pinning is implemented in iOS, here’s a link to the blog which will guide you in implementing SSL pinning in iOS.
Let’s come back to bypass part, there are 4 ways to do that:
- Frida
- Objection
- External application (Cydia)
- By modifying the IPA file
Let’s move on step by step
SSL pinning bypass using Frida for iOS¶
As you know already about Frida, basically it’s just used for hooking the application.\ Here basically we need to modify the application in runtime so that’s what Frida is used for, we can use Frida Gadget dynamic library to modify the application during run time, so what we will do is extract the IPA file then modify the binary to load Frida gadget, if we are changing or modifying the IPA file we need to code sign it for the IPA to work, code signing can be done by creating a developer account.
Once code signing is done repack the IPA and install the application.\ Looks complicated? right!\ Don’t worry objection is here to help you,
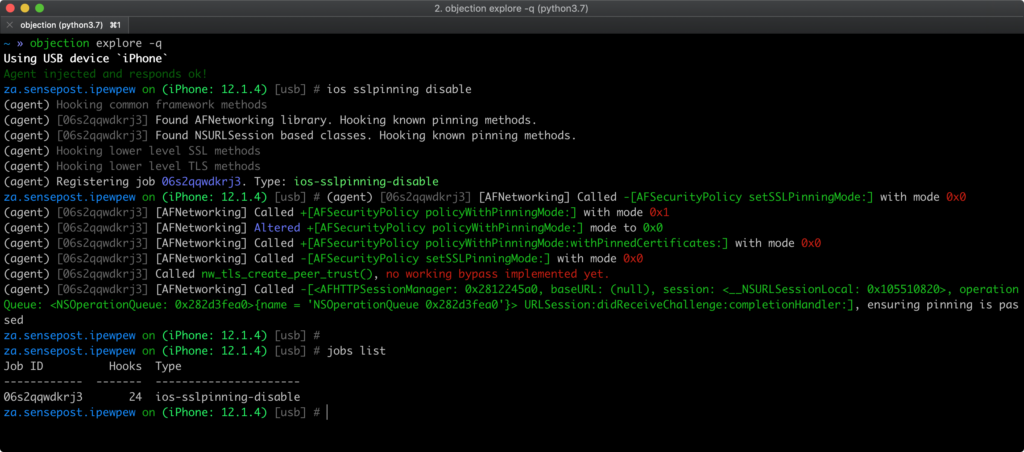
SSL pinning bypass using objection for iOS¶
Here it is simple as of android you need to install objection\ then use the command,
$ objection patchipa -s test.IPA -c 0[REDACTED]C
-s stands for the path to IPA file and
-c stands for code-signing certificate
Once done, install the modified application through ifunbox and run the
Use of external application¶
There are some external application such as SSL killswitch, just install it and bypass the SSL. It is as simple as its name, here you need a jailbroken device and remember Xposed framework for android same like that we have Cydia for iOS.\ So what is Cydia?\ Cydia installer is a free third-party app installer which is developed for the iOS devices. Think of Apple’s official App Store, this is similar to the app store which means you can download apps, games from the Cydia downloader, but there are many other advanced options that have been included in the Cydia free store, which is more than the official store.\ Thus, here you can find the “SSL killswitch“, install it and unpin the SSL for the application as you did it in android.
Modifying the IPA file¶
Most of the time the above methods should work. If not, this will definitely work, but here you need to know how the IPA application works, there is always an option to use disassemblers to be able to modify the IPA file to bypass any certificate validation. Some of the most common disassemblers are Hopper and IDA. Modifying the IPA will most likely break the signed application and it cannot be installed on an iOS device. Resigning the IPA file will allow you to install the mobile app.