Setting Up Frida+Objection¶
Here we would see how we can setup Frida, Objection, Fireprint Scanner for firebase DB scan, How to dump iPA file to perform Reverse Engineering and Static Analysis using Opensource Tool Mobsf. Also, look at how we use Frida to decrypt iOS files from the iDevice.
Let's have a short introduction to the following terms before proceeding further.
Frida¶
Frida is a free and open-source dynamic instrumentation toolkit, that allows developers, reverse-engineers, and security researchers to monitor and debug running processes. It also enables programmers, software and security professionals to execute their own JS scripts into other processes running on
Objection¶
It's a runtime mobile exploration toolkit, powered by Frida, built to help you assess the security posture of your mobile applications, without needing a jailbreak.
IPA File¶
It is a binary file that runs on iOS devices.
MobSF¶
Mobile Security Framework (MobSF) is an automated, open-source, all-in-one mobile application (Android/iOS/Windows) pen-testing framework capable of performing static, dynamic and malware analysis.
Fireprint¶
The fingerprint is a python based tool for finding misconfigured Firebase databases used in Android or iOS applications. Just drag and drop your apk/ipa files to this script and find if there is any misconfigured Firebase database is exists.
Installing Frida¶
a. We need to install Frida first to dump the IPA file. to install Frida simple execute following command in Linux box. You can use windows as well. I've already installed these tools.
sunil@ubuntu:~$ pip install frida-tools
b. To check the installed frida version use sunil@ubuntu:~$ frida --version
c. To install the Objection use pip install objection in the terminal. the use of objection we will see in the next post its mainly used for keychain dump, cookies dump, SSL pinning bypass, root/jailbreak-detection bypass and so more. Actually, the objection does the automated task while in Frida we need to do manually by writing the custom Javascript. So it's very handy to use for the pentester.
I'll show all this in the upcoming Blog Post.
As I have already installed so its showing requirement already satisfied.
d. To verify the installed version using the following command.
sunil@ubuntu:~$ objection version
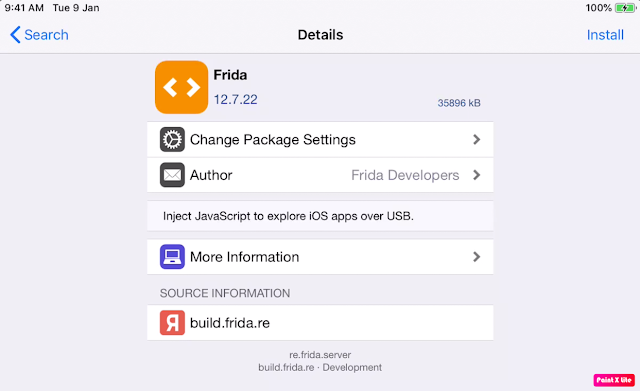
e. So After installing Frida-client on the machine, you need to install the Frida agents in the iDevice.
Just Open Cydia (Which is nothing but the play store for iOS) and add the repo http://build.re
f. Click on Add source.
g.Search for the frida in Cydia. and install it.
h. After done with installation. take an SSH of the device and execute the command While doing this make sure you connected via USB before using Frida. whenever we use Frida in ios we have to connect via USB. by using the switch -U
sunil@ubuntu:~$frida-ps -U
Where -U for USB. Once it's connected it shows all installed application names. we do a lot more with Frida like abuse the application logic by hooking, bypass the SSL pinning, Bypass login pin, enumeration classes, Bypass jailbreak detection and lot more. I'll show all this in the upcoming post on the DVIA app.
i. After installing all this requirement we need to install the python script which is used to dump/decrypt the iPA file.
You can download it from here: https://github.com/AloneMonkey/frida-ios-dump.git
Steps for installation¶
Open the terminal and clone the above Git URL
Now Go to Directory and Open dump.py file in nano editor.
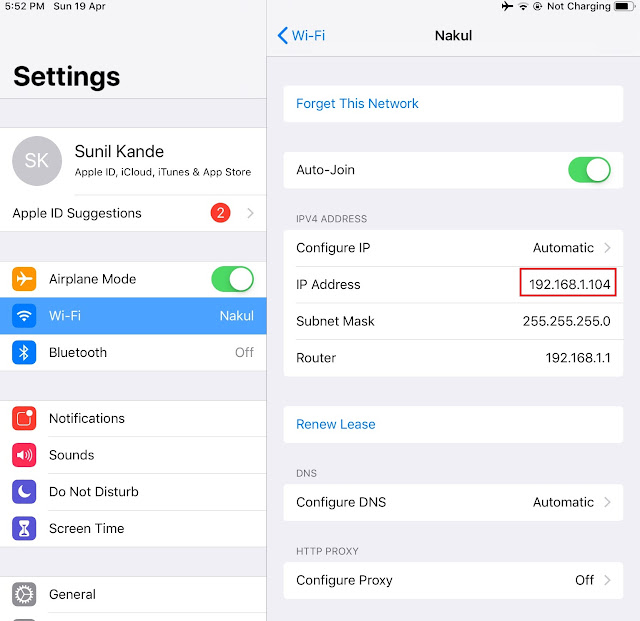
Here we need to collect some useful information. Just go to Setting => wifi and find the IP address. in my case, IP is 192.168.104 in your case it may be different.
Now open the dump.py file and replace the following things with your values.
**`Password - sunil Passwd of idevice`**
**`PORT - 22 (Port of SSH)`**
**`USER - root`**
**`HOST - 192.168.1.104`**
Do these respective changes and save the file.
In my case, it looks like.
Now go to the tool directory and run the tool by using the following command. python3 dump.py --help
As you see -l switch used to list all packages. **But remember while using this tool you should be connected to the PC via USB. Else it will give you an error**
As you can see below by using the switch -l tool fetches all installed app names and respective packages.\
To decrypt any iOS app just use package name after the dump.py script like
** python3 dump.py com.yahoo.rivals**
I'm using yahoo rivals app for demo purpose which I downloaded from the app store
While executing this command make a sure app which you want to decrypt that should be open on your device otherwise you won't able to decrypt it.\ \ You can see the decrypted IPA file present in the tool directory.\ \
Now, We can use IPA file for reverse engineering and for static analysis using tools like mobsf
For reverse engineering, We use tools like Hopper, IDA Pro. I'll write separate posts on these tools where we see how to use them and how we can analyze code to hook the app to bypasses some code restriction using Frida.!!!
But for now, I'm showing how we do static analysis of the application using mobsf
For this demo, we need to download tool Mobsf.
Download this tool by using the link.
Install using following simple commands.
root@ubuntu:~#git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF.git
root@ubuntu:~#cd Mobile-Security-Framework-MobSF
root@ubuntu:~#./setup.sh
As we see it start the server on http://0.0.0.0:8000
Open the server address in http://0.0.0.0:8000 in browser and import decrypted IPA file.
Now just import the IPA file which we decrypted using Frida dump tool and see the result as below.
- Basic information about the app and its binary file.
- Some options to View the Info.plist file.
- View the strings contained in the app binary.
- Download a class-dump, if the app was written in Objective-C; if it is written in Swift no class-dump can be created.
- List all Purpose Strings extracted from the Info.plist which give some hints on the app's permissions.
- Exceptions in the App Transport Security (ATS) configuration will be listed.
- A brief binary analysis showing if free binary security features are activated or e.g. if the binary makes use of banned APIs.
- List of libraries used by the app binary and list of all files inside the unzipped IPA.
- It is also helpful for finding out firebase credentials if there is any.
- Also, we can generate a pdf report to analyze all tested results.
Scan For Firebase Database
The fingerprint is a python based tool for finding misconfigured Firebase databases used in Android or iOS applications. Just drag and drop your apk/ipa files to this script and find if there is any misconfigured Firebase database is exists.
before installing tool we need to install some dependency tools. which are
Ref- https://github.com/sahad-mk/Fireprint
• clone the fireprint repo, git clone https://github.com/sahad-mk/Fireprint • Give executable permission, chmod +x fireprint.py
Sample use script - python3 fireprint.py -a test.ipa
We use the same IPA file for demo purposes.
\
\
If is there any data found then it will fetch for you. This is very useful when looking for any firebase credentials.\
\